Introduction
Port forwarding via SSH (SSH tunneling) creates a secure connection between a local computer and a remote machine through which services can be relayed. Because the connection is encrypted, SSH tunneling is useful for transmitting information that uses an unencrypted protocol, such as IMAP, VNC, or IRC.
Types of Port Forwarding
SSH's port forwarding feature can smuggle various types of Internet traffic into or out of a network. This can be used to avoid network monitoring or sniffers, or bypass badly configured routers on the Internet. Note: You might also need to change the settings in other programs (like your web browser) in order to circumvent these filters.
![]() Warning: Filtering and monitoring is usually implemented for a reason. Even if you don't agree with that reason, your IT department might not take kindly to you flouting their rules.
Warning: Filtering and monitoring is usually implemented for a reason. Even if you don't agree with that reason, your IT department might not take kindly to you flouting their rules.
There are three types of port forwarding with SSH:
- Local port forwarding: connections from the SSH client are forwarded via the SSH server, then ''to a destination server''
- Remote port forwarding: connections from the SSH server are forwarded via the SSH client, then to a destination server
- Dynamic port forwarding: connections from various programs are forwarded via the SSH client, then via the SSH server, and finally to several destination servers
Local port forwarding is the most common type. For example, local port forwarding lets you bypass a company firewall that blocks Wikipedia.
Remote port forwarding is less common. For example, remote port forwarding lets you connect from your SSH server to a computer on your company's intranet.
The goal of dynamic port forwarding is to enable clients to connect securely to a trusted server that acts as an intermediary for the purpose of sending/receiving data to one or many destination servers.
Dynamic port forwarding is implemented by setting up a local SOCKS proxy server with ssh client, which can be used to process data transmissions through the network or over the Internet.
Dynamic port forwarding is a powerful tool with many uses:
- A user connected to the Internet through a coffee shop, hotel, or otherwise minimally secure network may wish to use DPF as a way of protecting data.
- Can be used to bypass firewalls that restrict access to outside websites, such as in a corporate network.
- Can be used as a precaution against hacking.
Dynamic port forwarding over ssh is in a way a simple alternative to VPN.
To use port forwarding, you need to make sure port forwarding is enabled in your server. You also need to tell Core Tunnel the source and destination port numbers to use. If you're using local or remote forwarding, you need to tell Core Tunnel the destination server. If you're using dynamic port forwarding, you need to configure your programs to use a SOCKS proxy server.
Local Port Forwarding
Local port forwarding lets you connect from your local computer to another server. To use local port forwarding, you need to know your destination server, and two port numbers. You should already know your destination server, and for basic uses of port forwarding, you can usually use the port numbers in Wikipedia's list of TCP and UDP port numbers.
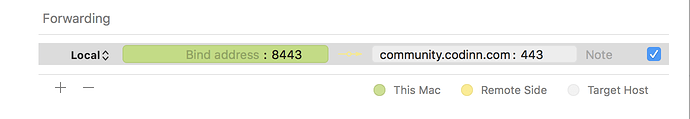
For example, say you wanted to connect from your laptop to https://community.codinn.com using an SSH tunnel. You would use source port number 8443 (the alternate https port), destination port 443 (the https port), and destination server community.codinn.com :
The equivalent ssh command:
ssh -L 8443:community.codinn.com:443 <host>
Where <host> should be replaced by the name of your laptop. The -L option specifies local port forwarding. For the duration of the SSH session, pointing your browser at https://localhost:8443/ would send you to https://community.codinn.com/.
In the above example, we used port 8443 for the source port. Ports numbers less than 1024 or greater than 49151 are reserved for the system, and some programs will only work with specific source ports, but otherwise you can use any source port number.
Remote Port Forwarding
Remote port forwarding lets you connect from the remote SSH server to another server. To use remote port forwarding, you need to know your destination server, and two port numbers. You should already know your destination server, and for basic uses of port forwarding, you can usually use the port numbers in Wikipedia's list of TCP and UDP port numbers.
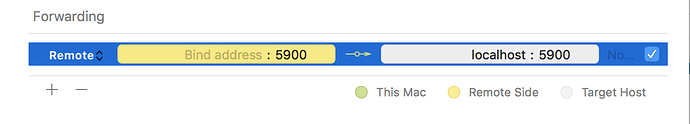
For example, say you wanted to let a friend access your Screen Sharing, using the command-line SSH client. You would use port number 5900 (the first VNC port), and destination server localhost:
The equivalent ssh command:
ssh -R 5900:localhost:5900 guest@joes-pc
The -R option specifies remote port forwarding. For the duration of the SSH session, Joe would be able to access your screen by connecting a VNC client to port 5900 on his computer (if you had set up a Screen Sharing).
Dynamic Port Forwarding
Dynamic port forwarding turns Core Tunnel into a SOCKS proxy server. SOCKS is a little-known but widely-implemented protocol for programs to request any Internet connection through a proxy server. Each program that uses the proxy server needs to be configured specifically, and reconfigured when you stop using the proxy server.
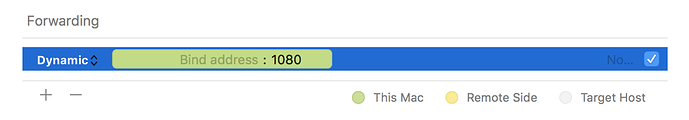
For example, say you wanted Firefox to connect to every web page through your SSH server. First you would use dynamic port forwarding with the default SOCKS port:
The equivalent ssh command:
ssh -D 1080 <host>
The -D option specifies dynamic port forwarding. 1080 is the standard SOCKS port. Although you can use any port number, some programs will only work if you use 1080.
Next you would tell Firefox to use your proxy, please consult this article to learn how to configure your web browser:
Reverse Dynamic Port Forwarding
A reverse dynamic port forwarding goes the opposite direction of a regular dynamic port forwarding. In a reverse dynamic port forwarding, a SOCKS port on the remote host is opened, and Core Tunnel will act as a SOCKS4/5 proxy and forward connections to destinations requested by the remote SOCKS client.
Reverse dynamic port forwarding is requested using extended syntax for the -R and RemoteForward options:
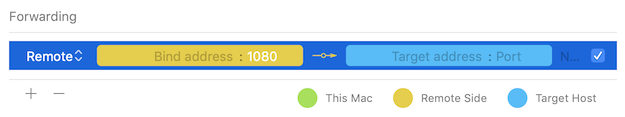
ssh -R 1080 <host>
In Core Tunnel (version 1.4.5 or later), you set forwarding type to Remote and leave target address and target port blank:
Port Forwarding Explained
To get the most out of port forwarding, it's helpful to know a bit about how the Internet works.
The Internet assigns computers virtual "ports", a bit like the USB ports on the back of your computer:
To let a digital camera share pictures with your PC, you connect the USB port on the camera to any USB port on the PC. The computer then talks to the camera about your photos, and shows you the result.
To let a web server share pages with your PC, you connect the web server port on the server to any Internet port on the PC. The computer then talks to the server about your page, and shows you the result.
Unlike a USB port, there is no physical component to an Internet port. There's no actual wire, or actual hole on the back of your computer. It's all just messages being sent over the Internet. Like other "virtual" computer concepts, Internet ports are just an analogy that help to explain what your computer is doing. Sometimes, that analogy breaks down:
There are two types of Internet port: normal "TCP" ports and strange "UDP" ports (which won't be covered here).
Unlike USB ports, every computer has exactly 65,535 numbered TCP ports, some of which have a special purpose. For example, port number 80 is your web server port, so your web browser knows it should connect to port number 80 in order to download a web page.
Connections between Internet ports can be patched together, so a connection from computer A to computer B on port 12,345 could be patched through to port number 80 on computer C. This is known as '''port forwarding'''.
Troubleshooting
If you get a message like this when you try to forward a port:
bind: Address already in use
channel_setup_fwd_listener: cannot listen to port: <port number>
Could not request local forwarding.
then someone is already listening on that port number. You won't be able to listen on that port until the other person has finished with it.
If forwarding doesn't seem to work, even though you didn't get a warning message, then your SSH server might have disabled forwarding. To check, do the following:
grep Forwarding /etc/ssh/sshd_config
If you see something like this:
X11Forwarding no
AllowTcpForwarding no
then forwarding is disabled on your server. See the SSH configuration page for more information.
This post, "What is port forwarding, and how to use it", is a derivative of "SSH/OpenSSH/PortForwarding" by "Contributors to the Ubuntu documentation wiki", used under CC BY-SA 3.0. "What is port forwarding, and how to use it" is licensed under CC BY-SA 3.0 by Codinn Technologies.