yang
January 1, 2019, 3:58am
1
Security and privacy are our number one priority.
The Core Shell / Core Tunnel 1.4.5 updates focus on security, all shipped binaries are now protected by the Hardened Runtime which was introduced in macOS Mojave.
In macOS Mojave, Apple has introduced support for Hardened Runtime:
Applications cannot debug other apps or be debugged themselves unless they explicitly declare that capability
Add the appropriate entitlement for each protected resource that your apps needs to access
Access still subject to user approval
Excerpt From: Your Apps and the Future of macOS Security - WWDC 2018
The hardened runtime prevents malicious software from accessing internal runtime data of the app, the drawback is this capability only available in macOS v10.14 and later.
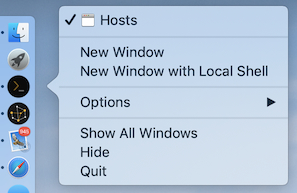
Quick open a new window from dock menu:
Suggested by @chrisj60 :
Another data point regarding the crash. If I close a session by closing the window (using the Mac red-dot close control) then Core Shell doesn’t crash. it only crashes if I exit a session cleanly using the shell ‘exit’ command or Ctrl-D.
Another request in the interests of usability. Right clicking on the dock icon when Core Shell is running ought to offer some app specific options such as New Window and New Tab.
Suggested by @chrisj60 :
You could do what iTerm2 does. If a new session is opened in a new tab, ignore the configured window size and use the one from the existing tab(s), if opening in a new window use the configured window size. Best of both worlds!
Another suggestion in the shell menu it would be great to have additional New Tab and New Window options with an arrow which goes to a list of the configured hosts so that you can open a new session to a specific host directly from the menu rather than have to open a new…
Suggested by @chrisj60 :
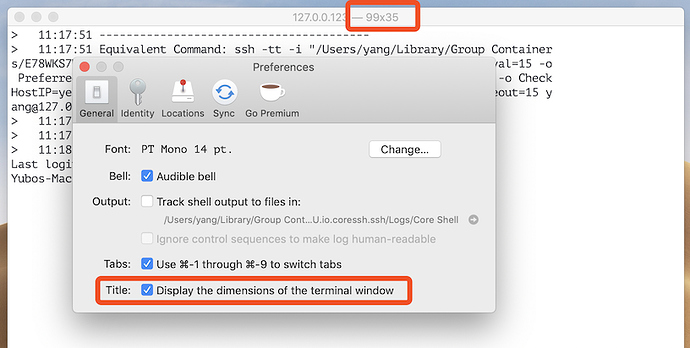
Remembering the last used size could be a workaround, but as far as I can see Core Shell doesn’t do that either (at least not if you close a session using the macOS ‘close window’ control). The other problem is that when re-sizing a window one has no idea what size you are resizing it to (in terms of terminal rows and columns) since, unlike other terminal apps, it doesn’t show the size as the window is being re-sized.
I’m a software engineer and I do most of my work via terminal/SSH sessions to…
Reported by @chrisj60 :
I’m running Core Shell v1.4 on macOS 10.14.2. Every time I close an SSH session (exit or Ctrl-D at shell prompt), Core Shell crashes (SIGSEGV). I’m using SSH Proxy and Core Tunnel without issue. Several crash reports have gone to Apple already. Currently Core Shell is unusable for me as a result of this issue.
The size and position of last closed main window should be remembered, reported by @chrisj60 :
Remembering the last used size could be a workaround, but as far as I can see Core Shell doesn’t do that either (at least not if you close a session using the macOS ‘close window’ control). The other problem is that when re-sizing a window one has no idea what size you are resizing it to (in terms of terminal rows and columns) since, unlike other terminal apps, it doesn’t show the size as the window is being re-sized.
I’m a software engineer and I do most of my work via terminal/SSH sessions to…
Please refer to section "Reverse Dynamic Port Forwarding" in post What is port forwarding, and how it works :
Reverse Dynamic Port Forwarding
A reverse dynamic port forwarding goes the opposite direction of a regular dynamic port forwarding. In a reverse dynamic port forwarding , a SOCKS port on the remote host is opened, and Core Tunnel will act as a SOCKS4/5 proxy and forward connections to destinations requested by the remote SOCKS client.
Reverse dynamic port forwarding is requested using extended syntax for the -R and RemoteForward options:
ssh -R 1080 <host>
In Core Tunnel (version 1.4.5 or later), you set forwarding type to Remote and leave target address and target port blank:
SSH: update the codebase of embedded OpenSSH XPC component from version 7.5 to 7.9
SSH: add RemoteCommand option to specify a command that will be executed on the remote host
SSH: add two new settings for StrictHostKeyChecking option: "accept-new" and "off"
SSH: add a BindInterface option to allow binding the outgoing connection to an interface's address
SSH: add a SetEnv directive to request that the server sets an environment variable in the session
SSH: add a CASignatureAlgorithms option to allow control over which signature formats are allowed for CAs to sign certificates
For password and interactive information items stored in system Keychain, the unique key should be the combination of login username, host address and port number.
Reported by @network :
Core Tunnel 1.3 remembers the password for SSH tunnels in the keychain, and it will always remember the last password stored.
However if switching between multiple tunnels it does not remember the password passwords other than the last one entered. This is frustrating when I am connecting to multiple tunnels a day. Is it a bug that it does not remember passwords other than the last tunnel used?
Internal sensitive runtime data exchanging is encrypted by asymmetric encryption
Reduce the app startup time
Other minor bug fixes
Add Chris Jenkins(@chrisj60 ), Brad Freeman(@network ) to special thanks
yang
January 14, 2019, 3:43am
3
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.