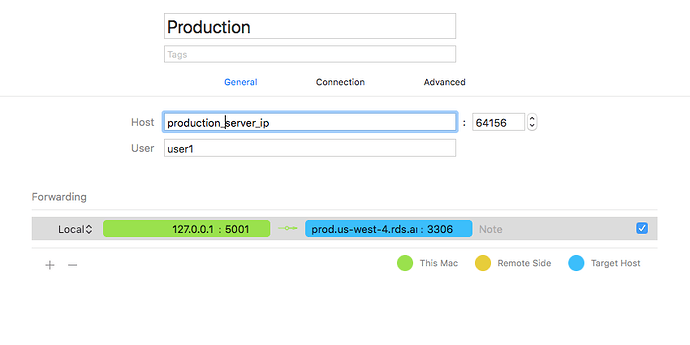
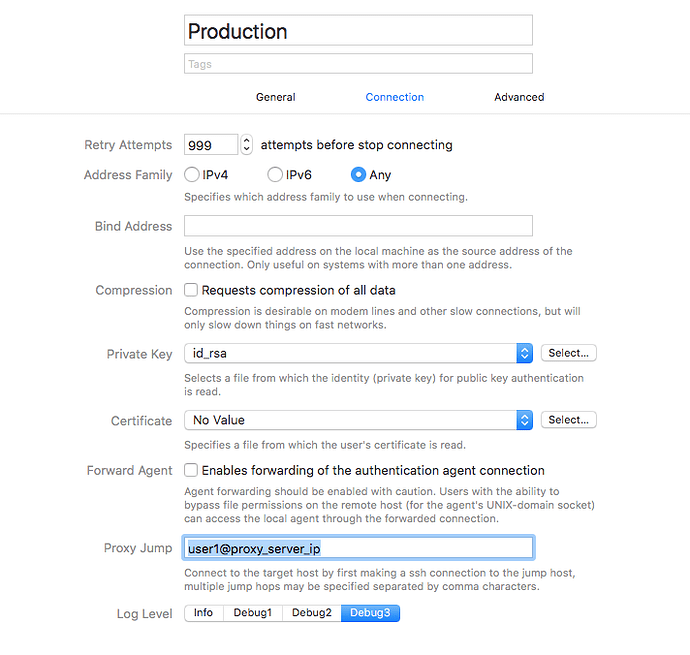
11.1.1.11 -> proxy server ip address
22.2.2.22 -> production server ip address
Equivalent Command: ssh -T -N -i "/Users/user1/Library/Group Containers/E78WKS7W4U.io.coressh.ssh/.ssh/privatekey/id_rsa" -J user1@11.1.1.11 -vvv -L 127.0.0.1:6111:prod.asfduihels.us-west-4.rds.amazonaws.com:3306 -o ServerAliveInterval=15 -o TCPKeepAlive=no -o ExitOnForwardFailure=yes -p 64156 user1@22.2.2.22
03:23:12 Connecting…
03:23:12 OpenSSH_7.5p1, LibreSSL 2.5.5
03:23:12 debug1: Reading configuration data /etc/ssh/ssh_config
03:23:12 debug1: /etc/ssh/ssh_config line 48: Applying options for *
03:23:12 debug1: /etc/ssh/ssh_config line 55: Applying options for 22.2.2.22
03:23:12 debug1: Setting implicit ProxyCommand from ProxyJump: ssh -l user1 -vvv -W '[%h]:%p' 11.1.1.11
03:23:12 debug1: Executing proxy xpc
03:23:12 debug1: key_load_public: No such file or directory
03:23:12 debug1: identity file /Users/user1/Library/Group Containers/E78WKS7W4U.io.coressh.ssh/.ssh/privatekey/id_rsa type -1
03:23:12 debug1: key_load_public: No such file or directory
03:23:12 debug1: identity file /Users/user1/Library/Group Containers/E78WKS7W4U.io.coressh.ssh/.ssh/privatekey/id_rsa-cert type -1
03:23:12 debug1: Enabling compatibility mode for protocol 2.0
03:23:12 debug1: Local version string SSH-2.0-OpenSSH_7.5
03:23:12 Jumping…
03:23:12 OpenSSH_7.5p1, LibreSSL 2.5.5
03:23:12 debug1: Reading configuration data /etc/ssh/ssh_config
03:23:12 debug1: /etc/ssh/ssh_config line 48: Applying options for *
03:23:12 debug2: resolving "11.1.1.11" port 22
03:23:12 debug2: ssh_connect_direct: needpriv 0
03:23:12 debug1: Connecting to 11.1.1.11 [11.1.1.11] port 22.
03:23:12 debug1: Connection established.
03:23:12 debug1: identity file /Users/user1/.ssh/id_rsa type 1
03:23:12 debug1: key_load_public: No such file or directory
03:23:12 debug1: identity file /Users/user1/.ssh/id_rsa-cert type -1
03:23:12 debug1: key_load_public: No such file or directory
03:23:12 debug1: identity file /Users/user1/.ssh/id_dsa type -1
03:23:12 debug1: key_load_public: No such file or directory
03:23:12 debug1: identity file /Users/user1/.ssh/id_dsa-cert type -1
03:23:12 debug1: key_load_public: No such file or directory
03:23:12 debug1: identity file /Users/user1/.ssh/id_ecdsa type -1
03:23:12 debug1: key_load_public: No such file or directory
03:23:12 debug1: identity file /Users/user1/.ssh/id_ecdsa-cert type -1
03:23:12 debug1: key_load_public: No such file or directory
03:23:12 debug1: identity file /Users/user1/.ssh/id_ed25519 type -1
03:23:12 debug1: key_load_public: No such file or directory
03:23:12 debug1: identity file /Users/user1/.ssh/id_ed25519-cert type -1
03:23:12 debug1: Enabling compatibility mode for protocol 2.0
03:23:12 debug1: Local version string SSH-2.0-OpenSSH_7.5
03:23:13 debug1: Remote protocol version 2.0, remote software version OpenSSH_7.6p1 Ubuntu-4ubuntu0.1
03:23:13 debug1: match: OpenSSH_7.6p1 Ubuntu-4ubuntu0.1 pat OpenSSH* compat 0x04000000
03:23:13 debug2: fd 4 setting O_NONBLOCK
03:23:13 debug1: Authenticating to 11.1.1.11:22 as 'user1'
03:23:13 debug3: hostkeys_foreach: reading file "/Users/user1/.ssh/known_hosts"
03:23:13 debug3: record_hostkey: found key type ECDSA in file /Users/user1/.ssh/known_hosts:30
03:23:13 debug3: load_hostkeys: loaded 1 keys from 11.1.1.11
03:23:13 debug3: order_hostkeyalgs: prefer hostkeyalgs: ecdsa-sha2-nistp256-cert-v01@openssh.com,ecdsa-sha2-nistp384-cert-v01@openssh.com,ecdsa-sha2-nistp521-cert-v01@openssh.com,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521
03:23:13 debug3: send packet: type 20
03:23:13 debug1: SSH2_MSG_KEXINIT sent
03:23:13 debug3: receive packet: type 20
03:23:13 debug1: SSH2_MSG_KEXINIT received
03:23:13 debug2: local client KEXINIT proposal
03:23:13 debug2: KEX algorithms: curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha256,diffie-hellman-group14-sha1,ext-info-c
03:23:13 debug2: host key algorithms: ecdsa-sha2-nistp256-cert-v01@openssh.com,ecdsa-sha2-nistp384-cert-v01@openssh.com,ecdsa-sha2-nistp521-cert-v01@openssh.com,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,ssh-ed25519-cert-v01@openssh.com,ssh-rsa-cert-v01@openssh.com,ssh-ed25519,rsa-sha2-512,rsa-sha2-256,ssh-rsa
03:23:13 debug2: ciphers ctos: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com,aes128-cbc,aes192-cbc,aes256-cbc
03:23:13 debug2: ciphers stoc: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com,aes128-cbc,aes192-cbc,aes256-cbc
03:23:13 debug2: MACs ctos: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
03:23:13 debug2: MACs stoc: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
03:23:13 debug2: compression ctos: none,zlib@openssh.com,zlib
03:23:13 debug2: compression stoc: none,zlib@openssh.com,zlib
03:23:13 debug2: languages ctos:
03:23:13 debug2: languages stoc:
03:23:13 debug2: first_kex_follows 0
03:23:13 debug2: reserved 0
03:23:13 debug2: peer server KEXINIT proposal
03:23:13 debug2: KEX algorithms: curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group14-sha256,diffie-hellman-group14-sha1
03:23:13 debug2: host key algorithms: ssh-rsa,rsa-sha2-512,rsa-sha2-256,ecdsa-sha2-nistp256,ssh-ed25519
03:23:13 debug2: ciphers ctos: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com
03:23:13 debug2: ciphers stoc: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com
03:23:13 debug2: MACs ctos: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
03:23:13 debug2: MACs stoc: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
03:23:13 debug2: compression ctos: none,zlib@openssh.com
03:23:13 debug2: compression stoc: none,zlib@openssh.com
03:23:13 debug2: languages ctos:
03:23:13 debug2: languages stoc:
03:23:13 debug2: first_kex_follows 0
03:23:13 debug2: reserved 0
03:23:13 debug1: kex: algorithm: curve25519-sha256
03:23:13 debug1: kex: host key algorithm: ecdsa-sha2-nistp256
03:23:13 debug1: kex: server->client cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none
03:23:13 debug1: kex: client->server cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none
03:23:13 debug3: send packet: type 30
03:23:13 debug1: expecting SSH2_MSG_KEX_ECDH_REPLY
03:23:13 debug3: receive packet: type 31
03:23:13 debug1: Server host key: ecdsa-sha2-nistp256 SHA256:D0RVU6WQrExjCksYxyEh3lEjusIb9Dp1rNWmo1qXhEU
03:23:13 debug3: hostkeys_foreach: reading file "/Users/user1/.ssh/known_hosts"
03:23:13 debug3: record_hostkey: found key type ECDSA in file /Users/user1/.ssh/known_hosts:30
03:23:13 debug3: load_hostkeys: loaded 1 keys from 11.1.1.11
03:23:13 debug1: Host '11.1.1.11' is known and matches the ECDSA host key.
03:23:13 debug1: Found key in /Users/user1/.ssh/known_hosts:30
03:23:13 debug3: send packet: type 21
03:23:13 debug2: set_newkeys: mode 1
03:23:13 debug1: rekey after 134217728 blocks
03:23:13 debug1: SSH2_MSG_NEWKEYS sent
03:23:13 debug1: expecting SSH2_MSG_NEWKEYS
03:23:13 debug3: receive packet: type 21
03:23:13 debug1: SSH2_MSG_NEWKEYS received
03:23:13 debug2: set_newkeys: mode 0
03:23:13 debug1: rekey after 134217728 blocks
03:23:13 debug2: key: /Users/user1/.ssh/id_rsa (0x7f8471c02c80)
03:23:13 debug2: key: /Users/user1/.ssh/id_dsa (0x0)
03:23:13 debug2: key: /Users/user1/.ssh/id_ecdsa (0x0)
03:23:13 debug2: key: /Users/user1/.ssh/id_ed25519 (0x0)
03:23:13 debug3: send packet: type 5
03:23:13 debug3: receive packet: type 7
03:23:13 debug1: SSH2_MSG_EXT_INFO received
03:23:13 debug1: kex_input_ext_info: server-sig-algs=<ssh-ed25519,ssh-rsa,rsa-sha2-256,rsa-sha2-512,ssh-dss,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521>
03:23:13 debug3: receive packet: type 6
03:23:13 debug2: service_accept: ssh-userauth
03:23:13 debug1: SSH2_MSG_SERVICE_ACCEPT received
03:23:13 debug3: send packet: type 50
03:23:13 debug3: receive packet: type 51
03:23:13 debug1: Authentications that can continue: publickey
03:23:13 debug3: start over, passed a different list publickey
03:23:13 debug3: preferred publickey,keyboard-interactive,password
03:23:13 debug3: authmethod_lookup publickey
03:23:13 debug3: remaining preferred: keyboard-interactive,password
03:23:13 debug3: authmethod_is_enabled publickey
03:23:13 debug1: Next authentication method: publickey
03:23:13 debug1: Offering RSA public key: /Users/user1/.ssh/id_rsa
03:23:13 debug3: send_pubkey_test
03:23:13 debug3: send packet: type 50
03:23:13 debug2: we sent a publickey packet, wait for reply
03:23:13 debug3: receive packet: type 60
03:23:13 debug1: Server accepts key: pkalg rsa-sha2-512 blen 535
03:23:13 debug2: input_userauth_pk_ok: fp SHA256:aZx9T7BRYqok735awNDBrZjpFG9qzSHyLcfIp+kag5g
03:23:13 debug3: sign_and_send_pubkey: RSA SHA256:aZx9T7BRYqok735awNDBrZjpFG9qzSHyLcfIp+kag5g
03:23:13 debug3: send packet: type 50
03:23:13 debug3: receive packet: type 52
03:23:13 debug1: Authentication succeeded (publickey).
03:23:13 Authenticated to 11.1.1.11 ([11.1.1.11]:22).
03:23:13 debug3: ssh_init_stdio_forwarding: 22.2.2.22:64156
03:23:13 debug1: channel_connect_stdio_fwd 22.2.2.22:64156
03:23:13 debug1: channel 0: new [stdio-forward]
03:23:13 debug2: fd 5 setting O_NONBLOCK
03:23:13 debug2: fd 6 setting O_NONBLOCK
03:23:13 debug1: getpeername failed: Bad file descriptor
03:23:13 debug3: send packet: type 90
03:23:13 debug2: fd 4 setting TCP_NODELAY
03:23:13 debug3: ssh_packet_set_tos: set IP_TOS 0x10
03:23:13 debug1: Requesting no-more-sessions@openssh.com
03:23:13 debug3: send packet: type 80
03:23:13 debug1: Entering interactive session.
03:23:13 debug1: pledge: network
03:23:13 debug2: fd 7 setting O_NONBLOCK
03:23:13 debug2: fd 8 setting O_NONBLOCK
03:23:14 debug3: receive packet: type 80
03:23:14 debug1: client_input_global_request: rtype hostkeys-00@openssh.com want_reply 0
03:23:14 debug3: receive packet: type 91
03:23:14 debug1: Remote protocol version 2.0, remote software version OpenSSH_7.2p2 Ubuntu-4ubuntu2.6
03:23:14 debug2: callback start
03:23:14 debug1: match: OpenSSH_7.2p2 Ubuntu-4ubuntu2.6 pat OpenSSH* compat 0x04000000
03:23:14 debug2: callback done
03:23:14 debug2: fd 5 setting O_NONBLOCK
03:23:14 debug2: channel 0: open confirm rwindow 2097152 rmax 32768
03:23:14 debug2: fd 4 setting O_NONBLOCK
03:23:14 debug1: Authenticating to 22.2.2.22:64156 as 'user1'
03:23:14 debug3: put_host_port: [22.2.2.22]:64156
03:23:14 Authenticating…
03:23:14 debug3: hostkeys_foreach: reading file "/Users/user1/.ssh/known_hosts"
03:23:14 debug3: record_hostkey: found key type ECDSA in file /Users/user1/.ssh/known_hosts:31
03:23:14 debug3: load_hostkeys: loaded 1 keys from [22.2.2.22]:64156
03:23:14 debug3: order_hostkeyalgs: prefer hostkeyalgs: ecdsa-sha2-nistp256-cert-v01@openssh.com,ecdsa-sha2-nistp384-cert-v01@openssh.com,ecdsa-sha2-nistp521-cert-v01@openssh.com,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521
03:23:14 debug3: send packet: type 20
03:23:14 debug1: SSH2_MSG_KEXINIT sent
03:23:14 debug3: receive packet: type 20
03:23:14 debug1: SSH2_MSG_KEXINIT received
03:23:14 debug2: local client KEXINIT proposal
03:23:14 debug2: KEX algorithms: curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha256,diffie-hellman-group14-sha1,ext-info-c
03:23:14 debug2: host key algorithms: ecdsa-sha2-nistp256-cert-v01@openssh.com,ecdsa-sha2-nistp384-cert-v01@openssh.com,ecdsa-sha2-nistp521-cert-v01@openssh.com,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,ssh-ed25519-cert-v01@openssh.com,ssh-rsa-cert-v01@openssh.com,ssh-ed25519,rsa-sha2-512,rsa-sha2-256,ssh-rsa
03:23:14 debug2: ciphers ctos: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com,aes128-cbc,aes192-cbc,aes256-cbc
03:23:14 debug2: ciphers stoc: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com,aes128-cbc,aes192-cbc,aes256-cbc
03:23:14 debug2: MACs ctos: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
03:23:14 debug2: MACs stoc: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
03:23:14 debug2: compression ctos: none,zlib@openssh.com,zlib
03:23:14 debug2: compression stoc: none,zlib@openssh.com,zlib
03:23:14 debug2: languages ctos:
03:23:14 debug2: languages stoc:
03:23:14 debug2: first_kex_follows 0
03:23:14 debug2: reserved 0
03:23:14 debug2: peer server KEXINIT proposal
03:23:14 debug2: KEX algorithms: curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group14-sha1
03:23:14 debug2: host key algorithms: ssh-rsa,rsa-sha2-512,rsa-sha2-256,ecdsa-sha2-nistp256,ssh-ed25519
03:23:14 debug2: ciphers ctos: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com
03:23:14 debug2: ciphers stoc: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com
03:23:14 debug2: MACs ctos: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
03:23:14 debug2: MACs stoc: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
03:23:14 debug2: compression ctos: none,zlib@openssh.com
03:23:14 debug2: compression stoc: none,zlib@openssh.com
03:23:14 debug2: languages ctos:
03:23:14 debug2: languages stoc:
03:23:14 debug2: first_kex_follows 0
03:23:14 debug2: reserved 0
03:23:14 debug1: kex: algorithm: curve25519-sha256@libssh.org
03:23:14 debug1: kex: host key algorithm: ecdsa-sha2-nistp256
03:23:14 debug1: kex: server->client cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none
03:23:14 debug1: kex: client->server cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none
03:23:14 debug3: send packet: type 30
03:23:14 debug1: expecting SSH2_MSG_KEX_ECDH_REPLY
03:23:14 debug3: receive packet: type 31
03:23:14 debug1: Server host key: ecdsa-sha2-nistp256 SHA256:ZCNRJFlO5jc5J4eUzrRllRHBWN8x1YIBz/wTjbqtFQM
03:23:14 debug3: put_host_port: [22.2.2.22]:64156
03:23:14 debug3: hostkeys_foreach: reading file "/Users/user1/.ssh/known_hosts"
03:23:14 debug3: record_hostkey: found key type ECDSA in file /Users/user1/.ssh/known_hosts:31
03:23:14 debug3: load_hostkeys: loaded 1 keys from [22.2.2.22]:64156
03:23:14 debug1: Host '[22.2.2.22]:64156' is known and matches the ECDSA host key.
03:23:14 debug1: Found key in /Users/user1/.ssh/known_hosts:31
03:23:14 debug3: send packet: type 21
03:23:14 debug2: set_newkeys: mode 1
03:23:14 debug1: rekey after 134217728 blocks
03:23:14 debug1: SSH2_MSG_NEWKEYS sent
03:23:14 debug1: expecting SSH2_MSG_NEWKEYS
03:23:14 debug3: receive packet: type 21
03:23:14 debug1: SSH2_MSG_NEWKEYS received
03:23:14 debug2: set_newkeys: mode 0
03:23:14 debug1: rekey after 134217728 blocks
03:23:14 debug2: key: /Users/user1/Library/Group Containers/E78WKS7W4U.io.coressh.ssh/.ssh/privatekey/id_rsa (0x0), explicit
03:23:14 debug3: send packet: type 5
03:23:14 debug3: receive packet: type 7
03:23:14 debug1: SSH2_MSG_EXT_INFO received
03:23:14 debug1: kex_input_ext_info: server-sig-algs=<rsa-sha2-256,rsa-sha2-512>
03:23:14 debug3: receive packet: type 6
03:23:14 debug2: service_accept: ssh-userauth
03:23:14 debug1: SSH2_MSG_SERVICE_ACCEPT received
03:23:14 debug3: send packet: type 50
03:23:14 debug3: receive packet: type 51
03:23:14 debug1: Authentications that can continue: publickey
03:23:14 debug3: start over, passed a different list publickey
03:23:14 debug3: preferred publickey,keyboard-interactive,password
03:23:14 debug3: authmethod_lookup publickey
03:23:14 debug3: remaining preferred: keyboard-interactive,password
03:23:14 debug3: authmethod_is_enabled publickey
03:23:14 debug1: Next authentication method: publickey
03:23:14 debug1: Trying private key: /Users/user1/Library/Group Containers/E78WKS7W4U.io.coressh.ssh/.ssh/privatekey/id_rsa
03:23:14 debug3: sign_and_send_pubkey: RSA SHA256:aZx9T7BRYqok735awNDBrZjpFG9qzSHyLcfIp+kag5g
03:23:14 debug3: send packet: type 50
03:23:14 debug2: we sent a publickey packet, wait for reply
03:23:14 debug3: receive packet: type 51
03:23:14 The Core Helper process exited or crashed.
03:23:14 The Core Helper connection has terminated.
03:23:14 The Core Helper connection has terminated.
03:23:14 Abnormal Disconnect