I am able to use this application as a SOCKS proxy, but when I set the socks proxy information in the MACOS Mojave system settings, I cannot connect to the internet as I do with chrome/vivaldi using explicit proxy settings that point to my core tunnel.
After changing system proxy settings, are you able to browse web sites with Safari?
no. I tried to restart safari too, but it made no difference.
Could you please enable logging and paste the log here? It can help me find the real cause.
I looked through the logs, but cannot see any errors of any kind...all I see when attempting to connect to a website in Safari is that packets are being sent and received:
10:58:44 debug3: send packet: type 80
10:58:44 debug3: receive packet: type 82
10:58:59 debug3: send packet: type 80
10:58:59 debug3: receive packet: type 82
10:59:14 debug3: send packet: type 80
10:59:14 debug3: receive packet: type 82
10:59:29 debug3: send packet: type 80
10:59:29 debug3: receive packet: type 82
10:59:44 debug3: send packet: type 80
10:59:44 debug3: receive packet: type 82
10:59:59 debug3: send packet: type 80
10:59:59 debug3: receive packet: type 82
11:00:14 debug3: send packet: type 80
11:00:15 debug3: receive packet: type 82
11:00:30 debug3: send packet: type 80
11:00:30 debug3: receive packet: type 82
11:00:45 debug3: send packet: type 80
11:00:45 debug3: receive packet: type 82
11:01:00 debug3: send packet: type 80
11:01:00 debug3: receive packet: type 82
11:01:15 debug3: send packet: type 80
11:01:15 debug3: receive packet: type 82
Please send me the connection log, so that I can check whether the tunnel was correctly configured.
Equivalent Command: ssh -NT -i "/Users/me/Library/Group Containers/E78WKS7W4U.io.coressh.ssh/.ssh/privatekey/id_rsa" -vvv -D 127.0.0.1:7777 -o ServerAliveInterval=15 -o ServerAliveCountMax=3 -o ExitOnForwardFailure=yes me@server.internal
10:53:41 Connecting…
10:53:41 Using Core Helper 4.0 (r40)
10:53:41 OpenSSH_7.9p1, OpenSSL 1.0.2q 20 Nov 2018
10:53:41 debug1: Reading configuration data /etc/ssh/ssh_config
10:53:41 debug1: /etc/ssh/ssh_config line 48: Applying options for *
10:53:41 debug2: resolve_canonicalize: hostname server.internal is address
10:53:41 debug2: ssh_connect_direct
10:53:41 debug1: Connecting to server.internal [1.2.3.4] port 22.
10:53:41 debug1: Connection established.
10:53:41 debug1: identity file /Users/me/Library/Group Containers/E78WKS7W4U.io.coressh.ssh/.ssh/privatekey/id_rsa type -1
10:53:41 debug1: identity file /Users/me/Library/Group Containers/E78WKS7W4U.io.coressh.ssh/.ssh/privatekey/id_rsa-cert type -1
10:53:41 debug1: Local version string SSH-2.0-OpenSSH_7.9
10:53:41 debug1: Remote protocol version 2.0, remote software version OpenSSH_7.4
10:53:41 debug1: match: OpenSSH_7.4 pat OpenSSH_7.0*,OpenSSH_7.1*,OpenSSH_7.2*,OpenSSH_7.3*,OpenSSH_7.4*,OpenSSH_7.5*,OpenSSH_7.6*,OpenSSH_7.7* compat 0x04000002
10:53:41 debug2: fd 3 setting O_NONBLOCK
10:53:41 debug1: Authenticating to server.internal:22 as 'me'
10:53:41 Authenticating…
10:53:41 debug3: hostkeys_foreach: reading file "/Users/me/.ssh/known_hosts"
10:53:41 debug3: record_hostkey: found key type ECDSA in file /Users/me/.ssh/known_hosts:13
10:53:41 debug3: load_hostkeys: loaded 1 keys from server.internal
10:53:41 debug3: order_hostkeyalgs: prefer hostkeyalgs: ecdsa-sha2-nistp256-cert-v01@openssh.com,ecdsa-sha2-nistp384-cert-v01@openssh.com,ecdsa-sha2-nistp521-cert-v01@openssh.com,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521
10:53:41 debug3: send packet: type 20
10:53:41 debug1: SSH2_MSG_KEXINIT sent
10:53:41 debug3: receive packet: type 20
10:53:41 debug1: SSH2_MSG_KEXINIT received
10:53:41 debug2: local client KEXINIT proposal
10:53:41 debug2: KEX algorithms: curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group14-sha256,diffie-hellman-group14-sha1,ext-info-c
10:53:41 debug2: host key algorithms: ecdsa-sha2-nistp256-cert-v01@openssh.com,ecdsa-sha2-nistp384-cert-v01@openssh.com,ecdsa-sha2-nistp521-cert-v01@openssh.com,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,ssh-ed25519-cert-v01@openssh.com,rsa-sha2-512-cert-v01@openssh.com,rsa-sha2-256-cert-v01@openssh.com,ssh-rsa-cert-v01@openssh.com,ssh-ed25519,rsa-sha2-512,rsa-sha2-256,ssh-rsa
10:53:41 debug2: ciphers ctos: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com
10:53:41 debug2: ciphers stoc: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com
10:53:41 debug2: MACs ctos: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
10:53:41 debug2: MACs stoc: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
10:53:41 debug2: compression ctos: none,zlib@openssh.com,zlib
10:53:41 debug2: compression stoc: none,zlib@openssh.com,zlib
10:53:41 debug2: languages ctos:
10:53:41 debug2: languages stoc:
10:53:41 debug2: first_kex_follows 0
10:53:41 debug2: reserved 0
10:53:41 debug2: peer server KEXINIT proposal
10:53:41 debug2: KEX algorithms: curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha256,diffie-hellman-group14-sha1,diffie-hellman-group1-sha1
10:53:41 debug2: host key algorithms: ssh-rsa,rsa-sha2-512,rsa-sha2-256,ecdsa-sha2-nistp256,ssh-ed25519
10:53:41 debug2: ciphers ctos: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com,aes128-cbc,aes192-cbc,aes256-cbc,blowfish-cbc,cast128-cbc,3des-cbc
10:53:41 debug2: ciphers stoc: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com,aes128-cbc,aes192-cbc,aes256-cbc,blowfish-cbc,cast128-cbc,3des-cbc
10:53:41 debug2: MACs ctos: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
10:53:41 debug2: MACs stoc: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
10:53:41 debug2: compression ctos: none,zlib@openssh.com
10:53:41 debug2: compression stoc: none,zlib@openssh.com
10:53:41 debug2: languages ctos:
10:53:41 debug2: languages stoc:
10:53:41 debug2: first_kex_follows 0
10:53:41 debug2: reserved 0
10:53:41 debug1: kex: algorithm: curve25519-sha256
10:53:41 debug1: kex: host key algorithm: ecdsa-sha2-nistp256
10:53:41 debug1: kex: server->client cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none
10:53:41 debug1: kex: client->server cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none
10:53:41 debug3: send packet: type 30
10:53:41 debug1: expecting SSH2_MSG_KEX_ECDH_REPLY
10:53:41 debug3: receive packet: type 31
10:53:41 debug1: Server host key: ecdsa-sha2-nistp256 SHA256:G/d+FCWr6IJyWG9T0RKWGgHXQOdzOWeO9N0kymCVcb0
10:53:41 debug3: hostkeys_foreach: reading file "/Users/me/.ssh/known_hosts"
10:53:41 debug3: record_hostkey: found key type ECDSA in file /Users/me/.ssh/known_hosts:13
10:53:41 debug3: load_hostkeys: loaded 1 keys from server.internal
10:53:41 debug1: Host 'server.internal' is known and matches the ECDSA host key.
10:53:41 debug1: Found key in /Users/me/.ssh/known_hosts:13
10:53:41 debug3: send packet: type 21
10:53:41 debug2: set_newkeys: mode 1
10:53:41 debug1: rekey after 134217728 blocks
10:53:41 debug1: SSH2_MSG_NEWKEYS sent
10:53:41 debug1: expecting SSH2_MSG_NEWKEYS
10:53:41 debug3: receive packet: type 21
10:53:41 debug1: SSH2_MSG_NEWKEYS received
10:53:41 debug2: set_newkeys: mode 0
10:53:41 debug1: rekey after 134217728 blocks
10:53:41 debug1: Will attempt key: /Users/me/Library/Group Containers/E78WKS7W4U.io.coressh.ssh/.ssh/privatekey/id_rsa explicit
10:53:41 debug2: pubkey_prepare: done
10:53:41 debug3: send packet: type 5
10:53:41 debug3: receive packet: type 7
10:53:41 debug1: SSH2_MSG_EXT_INFO received
10:53:41 debug1: kex_input_ext_info: server-sig-algs=<rsa-sha2-256,rsa-sha2-512>
10:53:42 debug3: receive packet: type 6
10:53:42 debug2: service_accept: ssh-userauth
10:53:42 debug1: SSH2_MSG_SERVICE_ACCEPT received
10:53:42 debug3: send packet: type 50
10:53:42 debug3: receive packet: type 51
10:53:42 debug1: Authentications that can continue: publickey,gssapi-keyex,gssapi-with-mic,keyboard-interactive
10:53:42 debug3: start over, passed a different list publickey,gssapi-keyex,gssapi-with-mic,keyboard-interactive
10:53:42 debug3: preferred publickey,keyboard-interactive,password
10:53:42 debug3: authmethod_lookup publickey
10:53:42 debug3: remaining preferred: keyboard-interactive,password
10:53:42 debug3: authmethod_is_enabled publickey
10:53:42 debug1: Next authentication method: publickey
10:53:42 debug1: Trying private key: /Users/me/Library/Group Containers/E78WKS7W4U.io.coressh.ssh/.ssh/privatekey/id_rsa
10:53:42 debug3: sign_and_send_pubkey: RSA SHA256:2Xve8rsHIUM8pb1v+8VVMvDsxUF2JU/imlJsThQkD84
10:53:42 debug3: sign_and_send_pubkey: signing using rsa-sha2-512
10:53:42 debug3: send packet: type 50
10:53:42 debug2: we sent a publickey packet, wait for reply
10:53:43 debug3: receive packet: type 52
10:53:43 debug1: Authentication succeeded (publickey).
10:53:43 Authenticated to server.internal ([server.internal]:22).
10:53:43 debug1: Local connections to 127.0.0.1:7777 forwarded to remote address socks:0
10:53:43 debug3: channel_setup_fwd_listener_tcpip: type 2 wildcard 0 addr 127.0.0.1
10:53:43 debug1: Local forwarding listening on 127.0.0.1 port 7777.
10:53:43 debug2: fd 4 setting O_NONBLOCK
10:53:43 debug3: fd 4 is O_NONBLOCK
10:53:43 debug1: channel 0: new [port listener]
10:53:43 debug2: fd 3 setting TCP_NODELAY
10:53:43 debug3: ssh_packet_set_tos: set IP_TOS 0x48
10:53:43 debug1: Requesting no-more-sessions@openssh.com
10:53:43 debug3: send packet: type 80
10:53:43 debug1: Entering interactive session.
10:53:43 debug1: pledge: network
10:53:43 Connected
10:53:43 debug2: fd 5 setting O_NONBLOCK
10:53:43 debug2: fd 6 setting O_NONBLOCK
10:53:43 debug3: receive packet: type 80
10:53:43 debug1: client_input_global_request: rtype hostkeys-00@openssh.com want_reply 0
10:53:58 debug3: send packet: type 80
10:53:58 debug3: receive packet: type 82
10:54:13 debug3: send packet: type 80
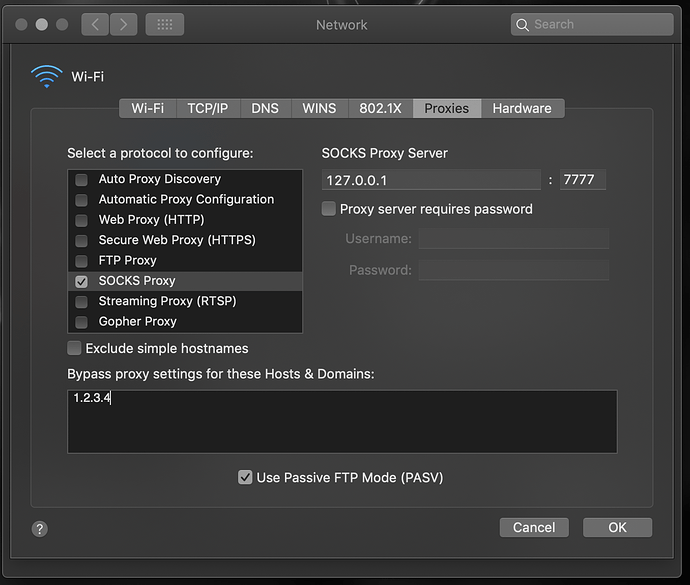
Thanks a lot for the log, could you please also send me a screenshot of your system proxy settings?
Thank you Aaron. From the log and screenshot, there is nothing wrong with your tunnel configuration.
I guess the problem is on the Remote side.
You can run this raw ssh command on Terminal:
ssh -i "/Users/me/Library/Group Containers/E78WKS7W4U.io.coressh.ssh/.ssh/privatekey/id_rsa" -vvv -D 127.0.0.1:7777 me@server.internal
And you will find still out of luck. Please check the remote side has the permission to access internet.
The remote side definitely can connect to the internet. When I use a different browser (Vivaldi) with a proxy plugin that directly uses the tunnel/proxy, everything is fine. It is when I use Safari, which has no separate proxy configuration settings that I cannot access the internet.
That is weird, could you please run this command and then paste the output?
lsof -nP -i4TCP:7777 | grep LISTEN
The above command will list who is listening on port 7070.
What is the proxy plugin you refer to for Chrome/Vivaldi? I have this setup working just fine but I mostly uses it with Firefox which is the only browser that natively can use a proxy different from the system.