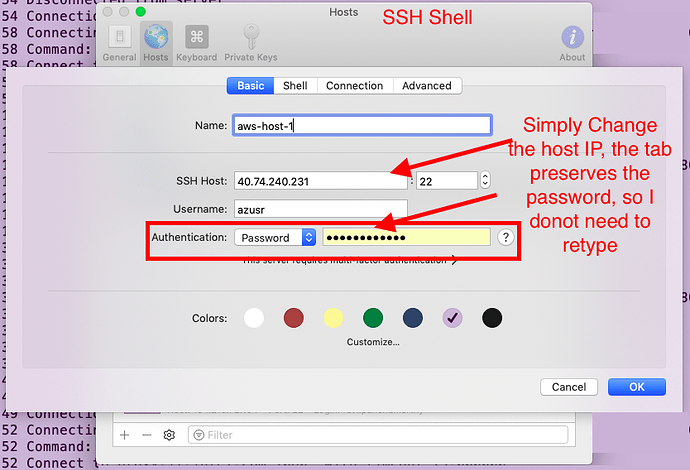
Having a password field in the settings, either in Connection or Advanced tab is useful.
Currently, pwd is saved per host ip. But when using the cloud services - like AWS, Azure or GCP, the host ip keeps changing but I prefer to use the same password.
Instead of IP address, you can use the domain name (e.g. examplevpz7.execute-api.us-west-2.amazonaws.com)
Core Shell use the host address (IP or domain name) as the primary key when saving password in keychain.
When we restart the cloud instance (launch, stop, start), both Public DNS(IPv4) and IPv4 Public IP address change. So we have to retype the password again.
For example:
At Launch:
Public DNS (IPv4): ec2-34-210-8-191.us-west-2.compute.amazonaws.com
IPv4 Public IP: 34.210.8.191
Stop the instance.
Start the same instance:
Public DNS (IPv4): ec2-54-212-42-211.us-west-2.compute.amazonaws.com
IPv4 Public IP: 54.212.42.211
Thanks for explanation. For this case, I would recommend you define something like this in your /etc/hosts:
34.210.8.191 dev-amazonaws
And in host settings, change Host to dev-amazonaws (or other name you chose)
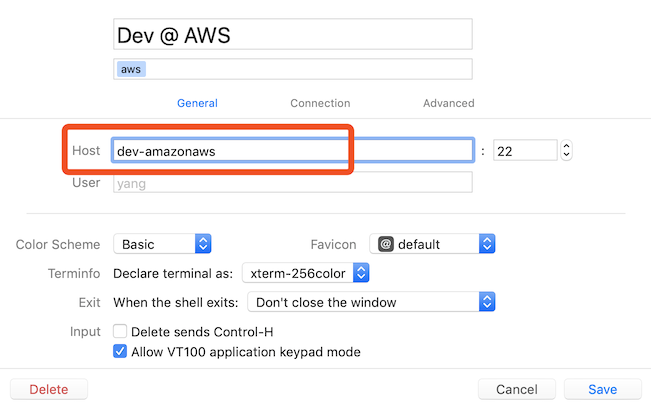
Core Shell would use the host name dev-amazonaws as the primary key when saving to keychain.
Every time after you restart the instance, edit /etc/hosts and change to the new address, then execute sudo killall -HUP mDNSResponder to force macOS flush DNS cache so that Core Shell can use the updated IP.
I think this is a little troublesome.。。
Thanks for the solution. It would be nice if this workflow is integrated in the Core Shell app itself.
The previous version "SSH Shell" used to save passwords in the connection tab itself which was easy !
SSH Shell and Core Shell make no difference on saving passwords. Though you can type in passwords in host settings, but they still be saved in system keychain, and also uses the host address as the primary key to fetch back. This means you still have to retype passwords after IP addresses changed in SSH Shell.
Another practical solution is to use public-key authentication, you don't have to retype the passphrase of the private key after IP address was changed.