I did try YubiKey 4 with Core Tunnel version 3.8.8 (53E56), and seemed every thing works. Here are the steps how I use YubiKey for testing:
-
Reset then initialize the YubiKey, follow steps in Authenticating SSH with PIV and PKCS#11 (client) to create keys.
-
Install OpenSC and create a tunnel with PKCS11Provider directive set to /Library/OpenSC/lib/opensc-pkcs11.so
-
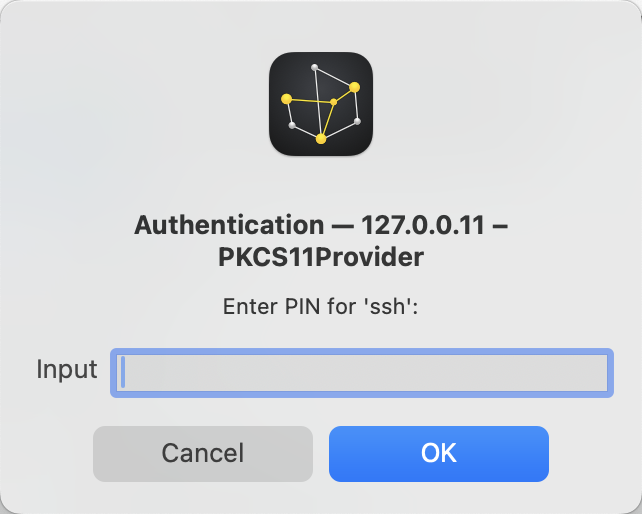
Connect the tunnel, and it shows using the YubiKey for authentication.
The PIN dialog:
Full connection log:
## 127.0.0.11 – PKCS11Provider ##
Equivalent Command: ssh -N -vvv -L 33333:codinn.com:22 -L 33334:localhost:22 -R localhost:3435:localhost:22 -o CheckHostIP=yes -o ServerAliveCountMax=3 -o ServerAliveInterval=15 -o PKCS11Provider=/Library/OpenSC/lib/opensc-pkcs11.so -o ConnectTimeout=15 -o TCPKeepAlive=no -o ExitOnForwardFailure=yes -p 22 yang@127.0.0.1
03:22:51 Connecting...
03:22:51 OpenSSH_8.8p1, OpenSSL 1.1.1l 24 Aug 2021
03:22:51 debug1: Reading configuration data /Users/yang/.ssh/config
03:22:51 debug1: Reading configuration data /etc/ssh/ssh_config
03:22:51 debug1: /etc/ssh/ssh_config line 21: include /etc/ssh/ssh_config.d/* matched no files
03:22:51 debug1: /etc/ssh/ssh_config line 54: Applying options for *
03:22:51 debug2: resolve_canonicalize: hostname 127.0.0.1 is address
03:22:51 debug3: expanded UserKnownHostsFile '~/.ssh/known_hosts' -> '/Users/yang/.ssh/known_hosts'
03:22:51 debug3: expanded UserKnownHostsFile '~/.ssh/known_hosts2' -> '/Users/yang/.ssh/known_hosts2'
03:22:51 debug3: ssh_connect_direct: entering
03:22:51 debug1: Connecting to 127.0.0.1 [127.0.0.1] port 22.
03:22:51 debug3: set_sock_tos: set socket 3 IP_TOS 0x48
03:22:51 debug2: fd 3 setting O_NONBLOCK
03:22:51 debug1: fd 3 clearing O_NONBLOCK
03:22:51 debug1: Connection established.
03:22:51 debug3: timeout: 15000 ms remain after connect
03:22:51 debug1: provider /Library/OpenSC/lib/opensc-pkcs11.so: manufacturerID <OpenSC Project> cryptokiVersion 2.20 libraryDescription <OpenSC smartcard framework> libraryVersion 0.25
03:22:51 debug1: provider /Library/OpenSC/lib/opensc-pkcs11.so slot 0: label <ssh> manufacturerID <piv_II> model <PKCS#15 emulate> serial <00000000> flags 0x40d
03:22:51 debug2: pkcs11_fetch_keys: provider /Library/OpenSC/lib/opensc-pkcs11.so slot 0: RSA SHA256:PdQXEDk9CVLzDOvOq1RuLFQ4FRCqe+CcpyKMCXLE4KE
03:22:51 debug1: have 1 keys
03:22:51 debug2: pkcs11_fetch_certs: provider /Library/OpenSC/lib/opensc-pkcs11.so slot 0: RSA SHA256:PdQXEDk9CVLzDOvOq1RuLFQ4FRCqe+CcpyKMCXLE4KE
03:22:51 debug2: pkcs11_fetch_certs: key already included
03:22:51 debug1: pkcs11_k11_free: parent 0x600003858160 ptr 0x600000f19960 idx 1
03:22:51 debug1: pkcs11_provider_unref: provider "/Library/OpenSC/lib/opensc-pkcs11.so" refcount 2
03:22:51 debug1: identity file /Users/yang/.ssh/id_rsa type 0
03:22:51 debug1: identity file /Users/yang/.ssh/id_rsa-cert type -1
03:22:51 debug1: identity file /Users/yang/.ssh/id_dsa type -1
03:22:51 debug1: identity file /Users/yang/.ssh/id_dsa-cert type -1
03:22:51 debug1: identity file /Users/yang/.ssh/id_ecdsa type -1
03:22:51 debug1: identity file /Users/yang/.ssh/id_ecdsa-cert type -1
03:22:51 debug1: identity file /Users/yang/.ssh/id_ecdsa_sk type -1
03:22:51 debug1: identity file /Users/yang/.ssh/id_ecdsa_sk-cert type -1
03:22:51 debug1: identity file /Users/yang/.ssh/id_ed25519 type 3
03:22:51 debug1: identity file /Users/yang/.ssh/id_ed25519-cert type -1
03:22:51 debug1: identity file /Users/yang/.ssh/id_ed25519_sk type -1
03:22:51 debug1: identity file /Users/yang/.ssh/id_ed25519_sk-cert type -1
03:22:51 debug1: identity file /Users/yang/.ssh/id_xmss type -1
03:22:51 debug1: identity file /Users/yang/.ssh/id_xmss-cert type -1
03:22:51 debug1: Local version string SSH-2.0-OpenSSH_8.8
03:22:51 debug1: Remote protocol version 2.0, remote software version OpenSSH_9.6
03:22:51 debug1: compat_banner: match: OpenSSH_9.6 pat OpenSSH* compat 0x04000000
03:22:51 debug2: fd 3 setting O_NONBLOCK
03:22:51 debug1: Authenticating to 127.0.0.1:22 as 'yang'
03:22:51 Authenticating...
03:22:51 debug3: record_hostkey: found key type ED25519 in file /Users/yang/.ssh/known_hosts:24
03:22:51 debug3: record_hostkey: found key type RSA in file /Users/yang/.ssh/known_hosts:25
03:22:51 debug3: record_hostkey: found key type ECDSA in file /Users/yang/.ssh/known_hosts:26
03:22:51 debug3: load_hostkeys_file: loaded 3 keys from 127.0.0.1
03:22:51 debug1: load_hostkeys: fopen /Users/yang/.ssh/known_hosts2: No such file or directory
03:22:51 debug1: load_hostkeys: fopen /etc/ssh/ssh_known_hosts: No such file or directory
03:22:51 debug1: load_hostkeys: fopen /etc/ssh/ssh_known_hosts2: No such file or directory
03:22:51 debug3: order_hostkeyalgs: have matching best-preference key type ssh-ed25519-cert-v01@openssh.com, using HostkeyAlgorithms verbatim
03:22:51 debug1: pkcs11_k11_free: parent 0x60000385c210 ptr 0x0 idx 1
03:22:51 debug3: send packet: type 20
03:22:51 debug1: SSH2_MSG_KEXINIT sent
03:22:51 debug3: receive packet: type 20
03:22:51 debug1: SSH2_MSG_KEXINIT received
03:22:51 debug2: local client KEXINIT proposal
03:22:51 debug2: KEX algorithms: curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group14-sha256,ext-info-c
03:22:51 debug2: host key algorithms: ssh-ed25519-cert-v01@openssh.com,ecdsa-sha2-nistp256-cert-v01@openssh.com,ecdsa-sha2-nistp384-cert-v01@openssh.com,ecdsa-sha2-nistp521-cert-v01@openssh.com,sk-ssh-ed25519-cert-v01@openssh.com,sk-ecdsa-sha2-nistp256-cert-v01@openssh.com,rsa-sha2-512-cert-v01@openssh.com,rsa-sha2-256-cert-v01@openssh.com,ssh-ed25519,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,sk-ssh-ed25519@openssh.com,sk-ecdsa-sha2-nistp256@openssh.com,rsa-sha2-512,rsa-sha2-256
03:22:51 debug2: ciphers ctos: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com
03:22:51 debug2: ciphers stoc: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com
03:22:51 debug2: MACs ctos: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
03:22:51 debug2: MACs stoc: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
03:22:51 debug2: compression ctos: none,zlib@openssh.com,zlib
03:22:51 debug2: compression stoc: none,zlib@openssh.com,zlib
03:22:51 debug2: languages ctos:
03:22:51 debug2: languages stoc:
03:22:51 debug2: first_kex_follows 0
03:22:51 debug2: reserved 0
03:22:51 debug2: peer server KEXINIT proposal
03:22:51 debug2: KEX algorithms: sntrup761x25519-sha512@openssh.com,curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group14-sha256,ext-info-s,kex-strict-s-v00@openssh.com
03:22:51 debug2: host key algorithms: rsa-sha2-512,rsa-sha2-256,ecdsa-sha2-nistp256,ssh-ed25519
03:22:51 debug2: ciphers ctos: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com
03:22:51 debug2: ciphers stoc: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com
03:22:51 debug2: MACs ctos: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
03:22:51 debug2: MACs stoc: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
03:22:51 debug2: compression ctos: none,zlib@openssh.com
03:22:51 debug2: compression stoc: none,zlib@openssh.com
03:22:51 debug2: languages ctos:
03:22:51 debug2: languages stoc:
03:22:51 debug2: first_kex_follows 0
03:22:51 debug2: reserved 0
03:22:51 debug1: kex: algorithm: curve25519-sha256
03:22:51 debug1: kex: host key algorithm: ssh-ed25519
03:22:51 debug1: kex: server->client cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none
03:22:51 debug1: kex: client->server cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none
03:22:51 debug3: send packet: type 30
03:22:51 debug1: expecting SSH2_MSG_KEX_ECDH_REPLY
03:22:51 debug3: receive packet: type 31
03:22:51 debug1: SSH2_MSG_KEX_ECDH_REPLY received
03:22:51 debug1: Server host key: ssh-ed25519 SHA256:wNVGzlFtM7LlDCIm1akQ/8r6bG7BJjWYq0DAcYSSjLs
03:22:51 debug3: record_hostkey: found key type ED25519 in file /Users/yang/.ssh/known_hosts:24
03:22:51 debug3: record_hostkey: found key type RSA in file /Users/yang/.ssh/known_hosts:25
03:22:51 debug3: record_hostkey: found key type ECDSA in file /Users/yang/.ssh/known_hosts:26
03:22:51 debug3: load_hostkeys_file: loaded 3 keys from 127.0.0.1
03:22:51 debug1: load_hostkeys: fopen /Users/yang/.ssh/known_hosts2: No such file or directory
03:22:51 debug1: load_hostkeys: fopen /etc/ssh/ssh_known_hosts: No such file or directory
03:22:51 debug1: load_hostkeys: fopen /etc/ssh/ssh_known_hosts2: No such file or directory
03:22:51 debug1: Host '127.0.0.1' is known and matches the ED25519 host key.
03:22:51 debug1: Found key in /Users/yang/.ssh/known_hosts:24
03:22:51 debug1: pkcs11_k11_free: parent 0x600003850580 ptr 0x0 idx 1
03:22:51 debug3: send packet: type 21
03:22:51 debug2: set_newkeys: mode 1
03:22:51 debug1: rekey out after 134217728 blocks
03:22:51 debug1: SSH2_MSG_NEWKEYS sent
03:22:51 debug1: expecting SSH2_MSG_NEWKEYS
03:22:51 debug3: receive packet: type 21
03:22:51 debug1: SSH2_MSG_NEWKEYS received
03:22:51 debug2: set_newkeys: mode 0
03:22:51 debug1: rekey in after 134217728 blocks
03:22:51 debug1: Will attempt key: PIV AUTH pubkey RSA SHA256:PdQXEDk9CVLzDOvOq1RuLFQ4FRCqe+CcpyKMCXLE4KE token
03:22:51 debug1: Will attempt key: /Users/yang/.ssh/id_rsa RSA SHA256:jT8FTKIyuj8CNzGCD6w2Bw+e172mxdTznx19SRQsNSg
03:22:51 debug1: Will attempt key: /Users/yang/.ssh/id_dsa
03:22:51 debug1: Will attempt key: /Users/yang/.ssh/id_ecdsa
03:22:51 debug1: Will attempt key: /Users/yang/.ssh/id_ecdsa_sk
03:22:51 debug1: Will attempt key: /Users/yang/.ssh/id_ed25519 ED25519 SHA256:brLSA5srpw6fDYS3YFG52aYQuZTLh4EW4FcfCAw8Npk
03:22:51 debug1: Will attempt key: /Users/yang/.ssh/id_ed25519_sk
03:22:51 debug1: Will attempt key: /Users/yang/.ssh/id_xmss
03:22:51 debug2: pubkey_prepare: done
03:22:51 debug3: send packet: type 5
03:22:51 debug3: receive packet: type 7
03:22:51 debug1: SSH2_MSG_EXT_INFO received
03:22:51 debug1: kex_input_ext_info: server-sig-algs=<ssh-ed25519,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,sk-ssh-ed25519@openssh.com,sk-ecdsa-sha2-nistp256@openssh.com,rsa-sha2-512,rsa-sha2-256>
03:22:51 debug1: kex_input_ext_info: publickey-hostbound@openssh.com (unrecognised)
03:22:51 debug1: kex_input_ext_info: ping@openssh.com (unrecognised)
03:22:51 debug3: receive packet: type 6
03:22:51 debug2: service_accept: ssh-userauth
03:22:51 debug1: SSH2_MSG_SERVICE_ACCEPT received
03:22:51 debug3: send packet: type 50
03:22:51 debug3: receive packet: type 51
03:22:51 debug1: Authentications that can continue: publickey,password,keyboard-interactive
03:22:51 debug3: start over, passed a different list publickey,password,keyboard-interactive
03:22:51 debug3: preferred publickey,keyboard-interactive,password
03:22:51 debug3: authmethod_lookup publickey
03:22:51 debug3: remaining preferred: keyboard-interactive,password
03:22:51 debug3: authmethod_is_enabled publickey
03:22:51 debug1: Next authentication method: publickey
03:22:51 debug1: Offering public key: PIV AUTH pubkey RSA SHA256:PdQXEDk9CVLzDOvOq1RuLFQ4FRCqe+CcpyKMCXLE4KE token
03:22:51 debug3: send packet: type 50
03:22:51 debug2: we sent a publickey packet, wait for reply
03:22:51 debug3: receive packet: type 60
03:22:51 debug1: Server accepts key: PIV AUTH pubkey RSA SHA256:PdQXEDk9CVLzDOvOq1RuLFQ4FRCqe+CcpyKMCXLE4KE token
03:22:51 debug3: sign_and_send_pubkey: RSA SHA256:PdQXEDk9CVLzDOvOq1RuLFQ4FRCqe+CcpyKMCXLE4KE
03:22:51 debug3: sign_and_send_pubkey: signing using rsa-sha2-512 SHA256:PdQXEDk9CVLzDOvOq1RuLFQ4FRCqe+CcpyKMCXLE4KE
03:22:51 debug1: read_passphrase: requested to askpass
03:23:06 debug1: pkcs11_k11_free: parent 0x600003850790 ptr 0x0 idx 1
03:23:06 debug1: pkcs11_k11_free: parent 0x600003840000 ptr 0x0 idx 1
03:23:06 debug1: pkcs11_check_obj_bool_attrib: provider "/Library/OpenSC/lib/opensc-pkcs11.so" slot 0 object 105553161716192: attrib 514 = 0
03:23:10 debug3: send packet: type 50
03:23:10 debug1: pkcs11_k11_free: parent 0x6000038540b0 ptr 0x0 idx 1
03:23:10 debug3: receive packet: type 52
03:23:10 debug1: pkcs11_k11_free: parent 0x6000038582c0 ptr 0x0 idx 1
03:23:10 debug1: pkcs11_k11_free: parent 0x600003858000 ptr 0x600000f4b180 idx 1
03:23:10 debug1: pkcs11_provider_unref: provider "/Library/OpenSC/lib/opensc-pkcs11.so" refcount 2
03:23:10 Authenticated to 127.0.0.1 ([127.0.0.1]:22) using "publickey".
03:23:10 debug1: check provider "/Library/OpenSC/lib/opensc-pkcs11.so"
03:23:10 debug1: pkcs11_provider_finalize: provider "/Library/OpenSC/lib/opensc-pkcs11.so" refcount 1 valid 1
03:23:10 debug1: pkcs11_provider_unref: provider "/Library/OpenSC/lib/opensc-pkcs11.so" refcount 1
03:23:10 debug1: Local connections to LOCALHOST:33333 forwarded to remote address codinn.com:22
03:23:10 debug3: channel_setup_fwd_listener_tcpip: type 2 wildcard 0 addr NULL
03:23:10 debug3: sock_set_v6only: set socket 5 IPV6_V6ONLY
03:23:10 debug1: Local forwarding listening on ::1 port 33333.
03:23:10 debug2: fd 5 setting O_NONBLOCK
03:23:10 debug3: fd 5 is O_NONBLOCK
03:23:10 debug1: channel 0: new [port listener]
03:23:10 debug1: Local forwarding listening on 127.0.0.1 port 33333.
03:23:10 debug2: fd 6 setting O_NONBLOCK
03:23:10 debug3: fd 6 is O_NONBLOCK
03:23:10 debug1: channel 1: new [port listener]
03:23:10 debug1: Local connections to LOCALHOST:33334 forwarded to remote address localhost:22
03:23:10 debug3: channel_setup_fwd_listener_tcpip: type 2 wildcard 0 addr NULL
03:23:10 debug3: sock_set_v6only: set socket 7 IPV6_V6ONLY
03:23:10 debug1: Local forwarding listening on ::1 port 33334.
03:23:10 debug2: fd 7 setting O_NONBLOCK
03:23:10 debug3: fd 7 is O_NONBLOCK
03:23:10 debug1: channel 2: new [port listener]
03:23:10 debug1: Local forwarding listening on 127.0.0.1 port 33334.
03:23:10 debug2: fd 8 setting O_NONBLOCK
03:23:10 debug3: fd 8 is O_NONBLOCK
03:23:10 debug1: channel 3: new [port listener]
03:23:10 debug1: Remote connections from localhost:3435 forwarded to local address localhost:22
03:23:10 debug3: send packet: type 80
03:23:10 debug1: ssh_init_forwarding: expecting replies for 1 forwards
03:23:10 debug2: fd 3 setting TCP_NODELAY
03:23:10 debug3: set_sock_tos: set socket 3 IP_TOS 0x48
03:23:10 debug1: Requesting no-more-sessions@openssh.com
03:23:10 debug3: send packet: type 80
03:23:10 debug1: Entering interactive session.
03:23:10 debug1: pledge: filesystem full
03:23:10 debug2: fd 9 setting O_NONBLOCK
03:23:10 debug2: fd 10 setting O_NONBLOCK
03:23:10 Connected
03:23:10 debug3: receive packet: type 80
03:23:10 debug1: client_input_global_request: rtype hostkeys-00@openssh.com want_reply 0
03:23:10 debug3: client_input_hostkeys: received RSA key SHA256:ua5jIGNjqD3rt8sXZlPn0T0pSB7BOwuoSwlgCqQl7R8
03:23:10 debug3: client_input_hostkeys: received ECDSA key SHA256:dGairz3UvCI2Dl9G/i4Um+wUwaHQQxRV0xCgqpasaeM
03:23:10 debug3: client_input_hostkeys: received ED25519 key SHA256:wNVGzlFtM7LlDCIm1akQ/8r6bG7BJjWYq0DAcYSSjLs
03:23:10 debug1: client_input_hostkeys: searching /Users/yang/.ssh/known_hosts for 127.0.0.1 / (none)
03:23:10 debug3: hostkeys_foreach: reading file "/Users/yang/.ssh/known_hosts"
03:23:10 debug1: pkcs11_k11_free: parent 0x600003850370 ptr 0x0 idx 1
03:23:10 debug1: pkcs11_k11_free: parent 0x600003850630 ptr 0x0 idx 1
03:23:10 debug1: pkcs11_k11_free: parent 0x600003850370 ptr 0x0 idx 1
03:23:10 debug1: pkcs11_k11_free: parent 0x600003850630 ptr 0x0 idx 1
03:23:10 debug1: pkcs11_k11_free: parent 0x600003850370 ptr 0x0 idx 1
03:23:10 debug1: pkcs11_k11_free: parent 0x600003850630 ptr 0x0 idx 1
03:23:10 debug3: hostkeys_find: found ssh-ed25519 key at /Users/yang/.ssh/known_hosts:24
03:23:10 debug3: hostkeys_find: found ssh-rsa key at /Users/yang/.ssh/known_hosts:25
03:23:10 debug1: pkcs11_k11_free: parent 0x6000038504d0 ptr 0x0 idx 1
03:23:10 debug3: hostkeys_find: found ecdsa-sha2-nistp256 key at /Users/yang/.ssh/known_hosts:26
03:23:10 debug1: pkcs11_k11_free: parent 0x600003850370 ptr 0x0 idx 1
03:23:10 debug3: hostkeys_find: found ssh-ed25519 key under different name/addr at /Users/yang/.ssh/known_hosts:32
03:23:10 debug1: pkcs11_k11_free: parent 0x6000038504d0 ptr 0x0 idx 1
03:23:10 debug1: pkcs11_k11_free: parent 0x600003850370 ptr 0x0 idx 1
03:23:10 debug1: pkcs11_k11_free: parent 0x600003850370 ptr 0x0 idx 1
03:23:10 debug1: pkcs11_k11_free: parent 0x600003850790 ptr 0x0 idx 1
03:23:10 debug1: pkcs11_k11_free: parent 0x600003850630 ptr 0x0 idx 1
03:23:10 debug1: pkcs11_k11_free: parent 0x600003850790 ptr 0x0 idx 1
03:23:10 debug1: pkcs11_k11_free: parent 0x600003850630 ptr 0x0 idx 1
03:23:10 debug1: pkcs11_k11_free: parent 0x600003850790 ptr 0x0 idx 1
03:23:10 debug1: pkcs11_k11_free: parent 0x600003850630 ptr 0x0 idx 1
03:23:10 debug1: pkcs11_k11_free: parent 0x600003850790 ptr 0x0 idx 1
03:23:10 debug1: pkcs11_k11_free: parent 0x600003850790 ptr 0x0 idx 1
03:23:10 debug1: pkcs11_k11_free: parent 0x600003850630 ptr 0x0 idx 1
03:23:10 debug1: pkcs11_k11_free: parent 0x6000038504d0 ptr 0x0 idx 1
03:23:10 debug1: pkcs11_k11_free: parent 0x600003850790 ptr 0x0 idx 1
03:23:10 debug1: pkcs11_k11_free: parent 0x6000038504d0 ptr 0x0 idx 1
03:23:10 debug1: pkcs11_k11_free: parent 0x600003850790 ptr 0x0 idx 1
03:23:10 debug1: client_input_hostkeys: searching /Users/yang/.ssh/known_hosts2 for 127.0.0.1 / (none)
03:23:10 debug1: client_input_hostkeys: hostkeys file /Users/yang/.ssh/known_hosts2 does not exist
03:23:10 debug3: client_input_hostkeys: 3 server keys: 0 new, 3 retained, 0 incomplete match. 0 to remove
03:23:10 debug1: client_input_hostkeys: no new or deprecated keys from server
03:23:10 debug1: pkcs11_k11_free: parent 0x6000038440b0 ptr 0x0 idx 1
03:23:10 debug3: receive packet: type 4
03:23:10 debug1: Remote: /Users/yang/.ssh/authorized_keys:1: key options: agent-forwarding port-forwarding pty user-rc x11-forwarding
03:23:10 debug3: receive packet: type 4
03:23:10 debug1: Remote: /Users/yang/.ssh/authorized_keys:1: key options: agent-forwarding port-forwarding pty user-rc x11-forwarding
03:23:10 debug3: receive packet: type 81
03:23:10 debug1: remote forward success for: listen localhost:3435, connect localhost:22
03:23:10 debug1: forwarding_success: all expected forwarding replies received
03:23:25 debug3: send packet: type 80
03:23:25 debug3: receive packet: type 82
03:23:40 debug3: send packet: type 80
03:23:40 debug3: receive packet: type 82
Could you please send me desensitized verbose connection logs? Both success and failure logs, these logs could help me identified problem.
Kindly Regards,
Yang
