It is possible to connect to another host via one or more intermediaries so that the client can act as if the connection were direct.
The main method is to use an SSH connection to forward the SSH protocol through one or more jump hosts, using the ProxyJump directive, to an SSH server running on the target destination host. This is the most secure method because encryption is end-to-end. In addition to whatever other encryption goes on, the end points of the chain encrypt and decrypt each other's traffic. So the traffic passing through the intermediate hosts is always encrypted. But this method cannot be used if either the intermediate hosts or the target host deny port forwarding.
When port forwarding is available the easiest way is to use ProxyJump in the configuration file or Proxy Jump in host settings. An example of Proxy Jump usage is:
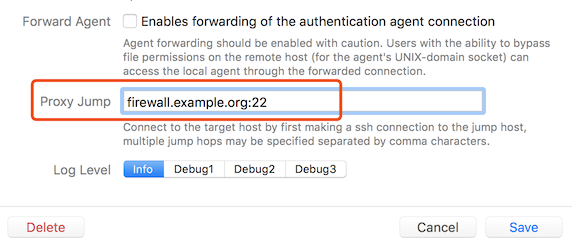
The equivalent ssh command:
$ ssh -J firewall.example.org:22 internal.example.org
ProxyJump Directive
Starting from OpenSSH 7.3, released August 2016, the easiest way to pass through one or more jump hosts is with the ProxyJump directive in ssh_config(5).
Host server2
HostName 192.168.5.38
ProxyJump user1@jumphost1.example.org:22
User fred
Multiple jump hosts can be specified as a comma-separated list. The hosts will be visited in the order listed.
Host server3
HostName 192.168.5.38
ProxyJump user1@jumphost1.example.org:22,user2@jumphost2.example.org:2222
User fred
It is not possible to use both the ProxyJump and ProxyCommand directives in the same host configuration. The first one found is used and then the other blocked.
This post, "Jump Hosts -- Passing Through a Gateway or Two", is a derivative of "OpenSSH/Cookbook/Proxies and Jump Hosts" by "Contributors to the Wikibooks", used under CC BY-SA 3.0. "Jump Hosts -- Passing Through a Gateway or Two" is licensed under CC BY-SA 3.0 by Codinn Technologies.